A research team at Darmstadt University of technology in Germany has just revealed a new way to load malware on the iPhone. Worse, attackers can even succeed when the device is turned off Although there is no evidence that the vulnerability has been exploited in the wild and may even need to be combined with other attack methods, it is still a hot potato for device manufacturer apple.
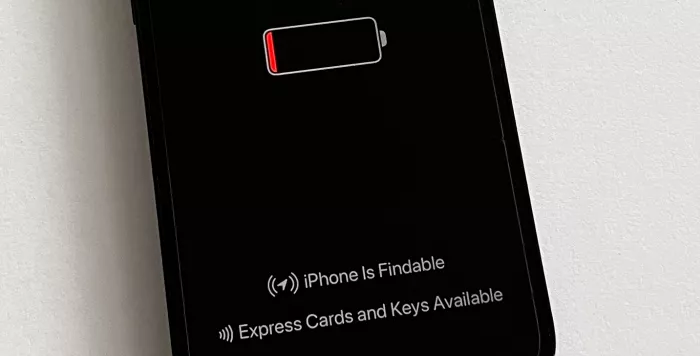
Research diagram - 1: iPhone Power reserve mode
TechSpot Note: this exploit is related to a feature in IOS 15 that allows find my to continue working for hours after the device is shut down.
Specifically, chips for Bluetooth, near field communication (NFC) and ultra wideband (UWB) will continue to operate in low power consumption (LPM) mode even after the user shuts down.
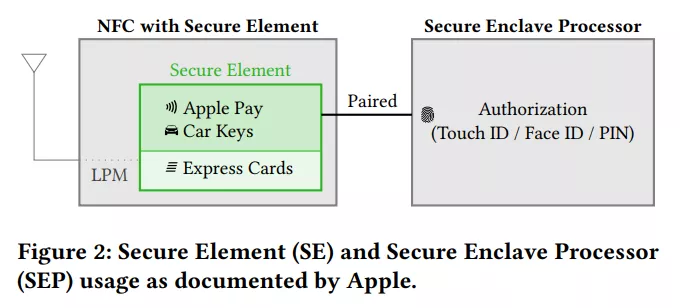
Research diagram - 2: Apple Schematic diagram of secure element and SEP secure enclave processor in official documents
This special mode is not the same as the "yellow battery indicator" turned on in the "low battery" state when you normally use iPhone.
It can be seen that when evaluating the LPM function, the research team of the University found that the Bluetooth LPM firmware was neither signed nor encrypted.
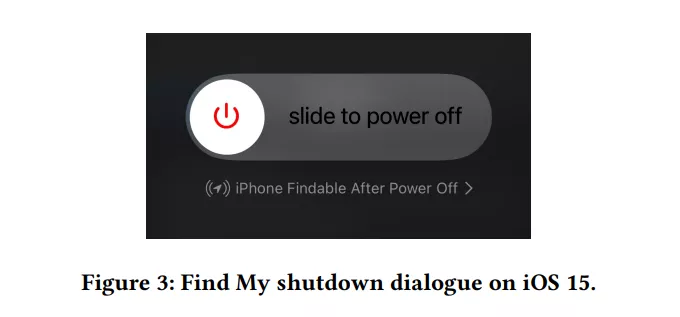
Figure 3: shutdown sliding dialog box of IOS 15
However, under the appropriate trigger conditions, the research team claimed that the firmware could be modified to run malware - conditions conducive to the attacker include jailbreaking the iPhone and preferably system level access.
If you have delegated power, the vulnerability exploitation of Bluetooth chip mentioned here may be superfluous. Even so, the researchers informed apple of the relevant problems in time, but the Cupertino technology giant did not immediately respond motherboard Request for comment.
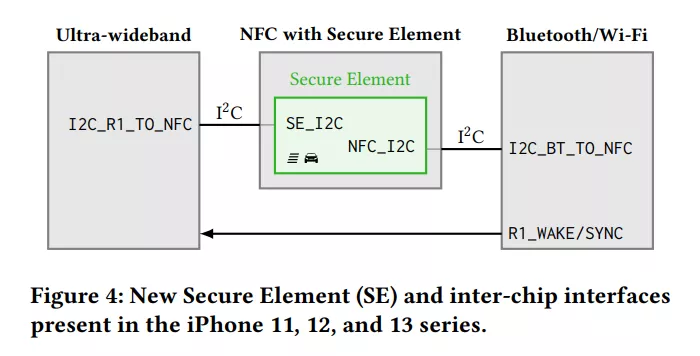
Figure 4: new secure element and on-chip interface on iPhone 11-13
Thanks to the lack of security, Ryan said, "it's difficult for attackers to launch attacks alone.".
However, if the attacker has the opportunity to directly exploit the Bluetooth chip and modify the firmware (it is not known that there are similar exploits), things will become quite tricky.
Even if the iPhone is turned off, hackers can still use this vulnerability to locate user devices.
Finally, arXiv preprint in May 2022 (PDF ) In the report, the research team warned that LPM is an attack surface that must be highly vigilant.
If people with ulterior motives get involved in deploying wireless malware on the iPhone after shutdown, the consequences will be unimaginable.