During the vision 2022 event held in Texas, Intel also took time to announce a new batch of security patches on Tuesday It can be seen that the 16 new announcements this month cover 41 vulnerabilities affecting its software and hardware, of which 76% were discovered by Intel engineers However, this article mainly introduces intel-sa-000617 / cve-2022-21151.
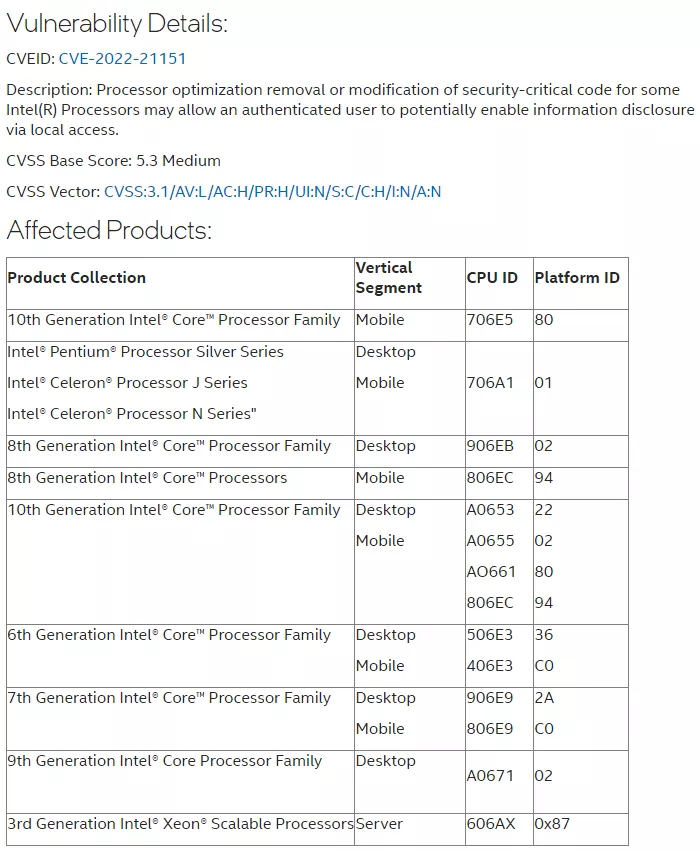
Screenshot (from Intel security center)
As a "medium" (5.3 / 10) security risk, it originates from the related security defects of Intel CPU or leads to the disclosure of information through local access.
Fortunately, today's newly released CPU microcode update has blocked this vulnerability. The official explained that the optimization can delete or modify the security critical code of some Intel processors, or allow authenticated users to access the leaked information locally.
In addition to the first Linux Security fix microcode update (20220510) covering CPUs from skylake / valley view to rocket Lake / Tiger lake and alder lake, the company also solved various functional problems.
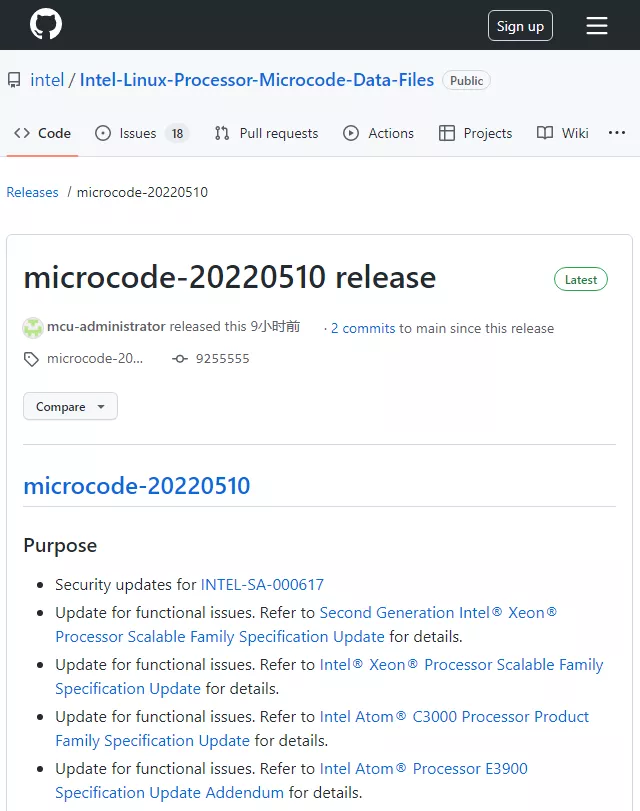
Intel CPU microcode updates for Linux users are available through GitHub Code hosting platform acquisition, windows Users are also requested to check for updates through windows update, or brush the new BIOS of the motherboard manufacturer.
As for Intel's other security announcements, you can move to today's security center View. These include local information disclosure patches for two Xeon platforms, and the potential denial of service of new firmware, boot guard and Intel SGX kernel drivers have also been alleviated.
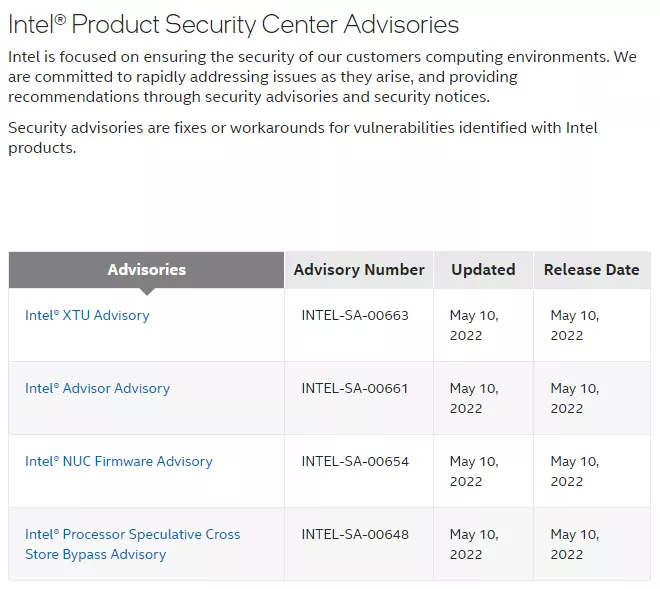
There is also a cross storage bypass vulnerability that affects the speculative execution of the processor. It can be seen that the behavior of some Intel CPUs is different, or allows authorized users to access potentially enabled information disclosure through local access, but the severity of the problem is relatively low.
Finally, Intel recommends enabling lfence load fence through potential gadgets to pay attention to the writing of the same shared memory address by another thread.