In the past, monitoring a person often required the placement of many bugging devices and a number of images to determine the individual's habits and movement patterns.

And nowadays, it's just a matter of hacking into your phone, which contains almost all of our personal preferences, habits, work and rest patterns, and even some health data.
Of course, these are the plots of many spy movies and are still far from our lives.
But for the world's specific professions, like politicians, investigative journalists, and corporate executives, there are often digital threats like being hacked.

▲ Barack Obama with a Blackberry
They may be a tiny minority of the world's population, highly negligible in statistics, but when their phones are exploited by malware, the ripple effect can be quite large.
Creating a set of tough security initiatives for this potentially less than 1% of the population may not be a huge investment of resources for large tech companies.

▲ Biden is already using a custom iPhone
I vaguely remember that during Obama's tenure, the US dignitaries were collectively equipped with customized BlackBerrys. With the gradual retirement of BlackBerry, iOS and Android devices have become the only choice, and the NSA will also make encryption or restrict the functions of the corresponding products to avoid the smart devices by the corresponding hacking and eavesdropping.
It's just that such an approach is not geared towards all users who are at risk of being cyber-attacked, and the 'vulnerability' is still there.
Apple Lockdown mode, coming in the fall
Apple, which has always touted a focus on privacy and data protection, has gone live with a Lockdown (lockdown) mode today along with the iOS 16 beta. Designed to keep all Apple devices safe from extreme digital threats from
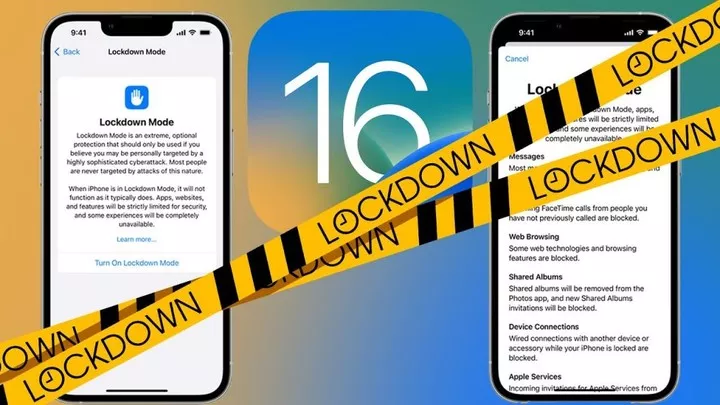
▲ Image from: edcocp
Meanwhile, Lockdown mode will be pushed to all Apple devices in the world along with the official release of iOS 16, iPadOS 16, and macOS Ventura.
Doing so, naturally, includes the much-needed Lockdown mode to protect the few users who are vulnerable to digital threats.
Apple's official website also concludes with an official definition for the Lockdown mode protection function is officially defined.
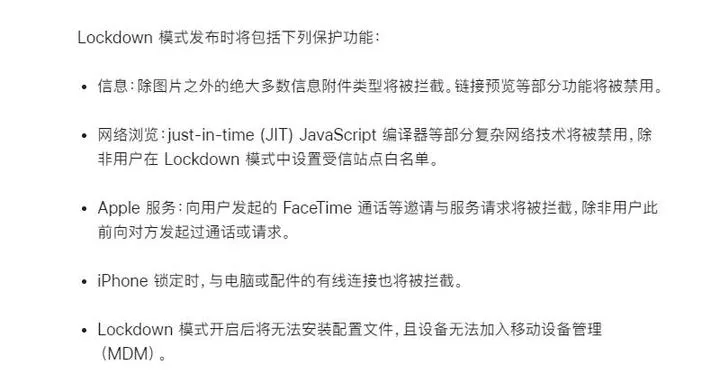
Basically, it revolves around information, networking, Apple services, accessories, etc. Apple will continue to pour resources into Lockdown mode and continue to add protection.
Apple has also created a new category in its Apple Security Bounty program to reward white hackers who find vulnerabilities in Lockdown mode and suggest enhancements. And it's doubled the prize money to an industry-capped $2 million.

In addition to inspiring its own security programs, Apple also donated $10 million to the Dignity and Justice Fund, which supports organizations that investigate, expose, and prevent highly targeted cyber attacks.
After the launch of this feature, Apple received almost unanimous praise. Not only Apple, but tech companies like Google and Meta have suffered digital threats from a number of hacker groups, although all have supposed initiatives in place.

But Apple's stance is not one of cover-up, but rather a frank admission that a small number of its devices are under attack by hacker groups, and that Lockdown brings with it a lack of common functionality.
In addition, Lockdown mode is very simple, just like setting an alarm clock, one switch is enough. It does not matter if you are high risk or general population, you can use it as long as you need it, no additional settings are needed.
As well, Lockdown mode is a move to popularize security to the average user, rather than a brutal and direct shutdown or destruction of the phone like in the movie.

Commenting on the launch of Lockdown mode, Ivan Krstić, Apple's head of security engineering and architecture, said in an external statement "Lockdown is a groundbreaking feature that reflects our unwavering commitment to protecting users from the rarest and most sophisticated attacks."
And these sophisticated and rare cyber attacks are not just in the movies - spyware makers like NSO Group, Candiru, and Cytrox exist in reality.
Spies are all around us
Perhaps unlike what we think, hacking into a mobile phone is not simple, nor can it be done easily by one person.

▲ NSO Group from Israel Photo by: wired
NSO Group, Candiru, who provide the service, are more like a software manufacturer who spends a lot of money and resources to roll out software that exploits vulnerabilities and then accepts demand attacks.
On a smaller scale, it's a bit like Party A and Party B. On a larger scale, it's a private contractor running into battle.

▲ Image from: static
One of the bigger names, NSO, has developed tools such as Pegasus for iOS and Android, which can target intrusions by phone number.
They send a message to the target phone that launches a 'Zero-Click' attack whether the user clicks on it or not, thus controlling the device as a tool to collect and send back sensitive information.

According to a previous Bloomberg report, employees of the U.S. government have received notifications from Apple for malicious attacks over the past few years.
Users in 150 other countries have also received Apple notifications, so the reach is wide and the number is growing.
Apple subsequently released a software update for Pegesus as well, and sued the NSO Group, claiming that Pegasus spyware from NSO severely violated the privacy of Apple users.

In fact, it's not just Apple, Microsoft and Google have also suffered from NSO intrusions. Recently, Pegasus has been on the US trade blacklist to stop Pegasus abuse.
And now that the Lockdown model is online, it certainly continues to limit Pegasus' continued expansion.
It is foreseeable that Google, Microsoft, and Meta will all make similar moves after Apple's Lockdown model goes live.
The game of intrusion and anti-intrusion
Pegasus was originally developed by the NSO Group to combat terrorism, and its customers were initially government agencies around the world.

▲ Craig Federighi, Senior Vice President, Apple Software
Craig Federighi, Apple's senior vice president of software, says NSO is not regulated and likewise has no effective accountability mechanisms, yet it has been able to spend millions of dollars on sophisticated surveillance technology to develop "notorious" software like Pegasus.
According to the New York Times in 2016, NSO can customize Pegasus software to the user's needs and hack into the target's phone, a package that costs at least $500,000.
At the same time, NSO also offered packages such as discounts on large orders, and also offered maintenance fees similar to annual packages, etc. By that time, NSO had a complete chain of profitability in place.

NSO claims that the clients are mostly national and regional, but there is no so-called audit itself, and the authenticity is doubtful.
Also, in an interview with Calcalist, Shalev Hulio, CEO of NSO Group, said that NSO has roughly 45 customers per year, with a total of about 100 Pegasus targets.
and emphasized that if NSO finds that customers are not using Pegasus as intended, NSO will cut off access between them, but without a third-party regulator, such a statement remains in doubt.
Meanwhile, from the leaked promotional material, NSO does not believe Pegasus will be affected by the iOS and Android upgrades, as it is itself taking advantage of more vulnerabilities to upgrade Pegasus' capabilities.

▲ Image from: BBC
With Pegasus becoming more widely targeted and more frequent, and with regular software updates to fix vulnerabilities no longer being able to be blocked, Apple introduced Lockdown mode to all users, which is like a game of chance.
And Apple isn't stopping at the existing Lockdown mode, it will still continue to add features and close loopholes.

The NSO-developed Pegasus is extremely expensive to use, and at close to a million dollars, it's clear that it won't be used on a large scale for the average user. Apple's introduction of the Lockdown model for a very small audience is arguably a way to protect every user's data and an expression of technology for good.
If we go even bigger, Apple is using its influence to move the security industry forward in a simple and effective way.