The cryptocurrency community has long believed that the digital addresses of bitcoin and other wallets will protect the identity of those who use them for trading A new paper published this week by researchers at Baylor College of medicine and Rice University breaks this supposed anonymity
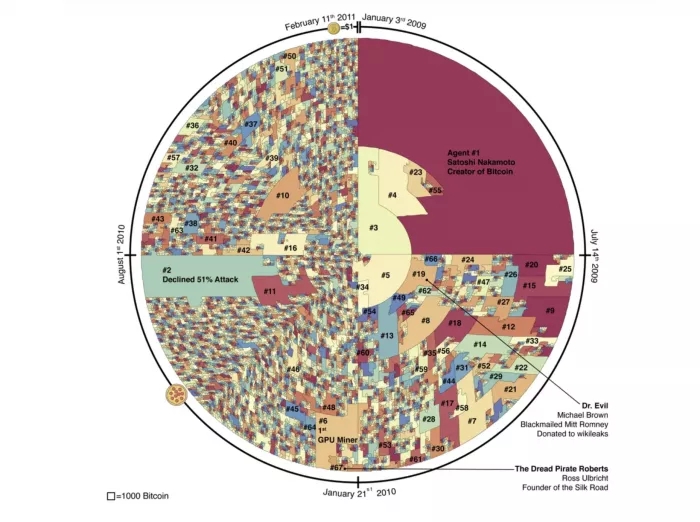
Researchers used a technology called "address linking" to study the transactions in the first two years after the establishment of bitcoin, that is, from January 2009 to February 2011. Their key discovery is that in the first two years, most bitcoins were mined by 64 agents, with a total value of $84billion at current prices. This figure is 1000 times smaller than the previous estimate of the size of the early bitcoin community (75000 people).
These 64 people include some famous figures who have become legends, such as Ross Ulbricht, whose name is "Roberts the fear pirate". Ulbritt was the founder of the "Silk Road", a black market that used bitcoin for illegal activities until it was closed by the FBI. After the introduction of bitcoin and its parity with the US dollar, 64 agents mined most of bitcoin.
Researchers used data leakage to build a blockchain map in early 2011, in which bitcoin is arranged according to mining agents. The research focuses on the impact of people participating in game theory as anonymous parties. Surprisingly, they found that early insiders like Ulbricht could take advantage of the relative scarcity of participants by destroying bitcoin to achieve dual consumption of bitcoin, but they did not. Their behavior is "altruistic" to maintain the integrity of the system. This is intriguing, but a more urgent discovery is that addresses can be traced and identities can be revealed.
In order to find out who was doing these early transactions, the team had to reverse design the entire premise of bitcoin and all cryptocurrencies: anonymity. As Nakamoto outlined in the original bitcoin white paper, privacy will be protected in two ways: anonymously using the public key and creating a new key pair for each transaction. The traditional banking model achieves a certain degree of privacy by restricting the access of relevant parties and trusted third parties to information. The need to publicly announce all transactions precludes this approach, but privacy can still be maintained by breaking the flow of information in another place: by maintaining the anonymity of the public key. The public can see that someone is sending an amount to others, but there is no information linking the transaction to anyone.
As an additional firewall, each transaction should use a new key pair to prevent them from being linked to a common owner. For multi input transactions, some links are still inevitable, which inevitably shows that their input is owned by the same owner. The risk is that if the owner of a key is revealed, the link may reveal other transactions belonging to the same owner.
Blackburn and the team had to trace these key pairs to reveal the traders of early bitcoin. To do this, they developed the so-called novel address linking scheme. Two of these technologies take advantage of how bitcoin mining software generates apparently meaningless strings that are used as part of bitcoin's encryption protection against forgery. In fact, there is a wide range of associations between seemingly meaningless strings related to a user. The other two technologies take advantage of unsafe user behavior, such as using multiple addresses to pay for a transaction, which makes it possible to link addresses according to transaction activities.
The consequence, they wrote, is that it is possible to "follow the money", starting with a known identity and exposing any identity by tracking the relevance chain in the address graph. These network attributes will have unexpected privacy consequences, because they make it easier for the network to be anonymized using the "follow the money" method. In this method, the identity of the target bitcoin address can be determined by identifying a short transaction path, which is connected to an address with known identity, and then use the data source outside the chain (from public data to subpoena) to walk along the path to determine who pays who will eliminate the identity of the address until the target address is identified.