In the mainstream concept, the security of Linux based distribution version is higher than that of windows and MacOS. This is because it is less mainstream than the latter two, and the more important reason is that it is safe enough But that doesn't mean there's no malware for Linux, BlackBerry And intel labs Our research team recently discovered symbiote malware

The destructive power of symbiote is worrying. It is described as "almost impossible to detect". It is also an extremely dangerous malware. It "parasitizes" the system, infects all running processes, and provides rootkit functions and remote access for threat participants.
"Symbiote" is a biological term for symbiosis or parasitism with another organism. Symbiote malware also has such characteristics. It was discovered as early as November 2021. It seems to be specially developed for the financial sector.
About symbiote malware, security researchers said
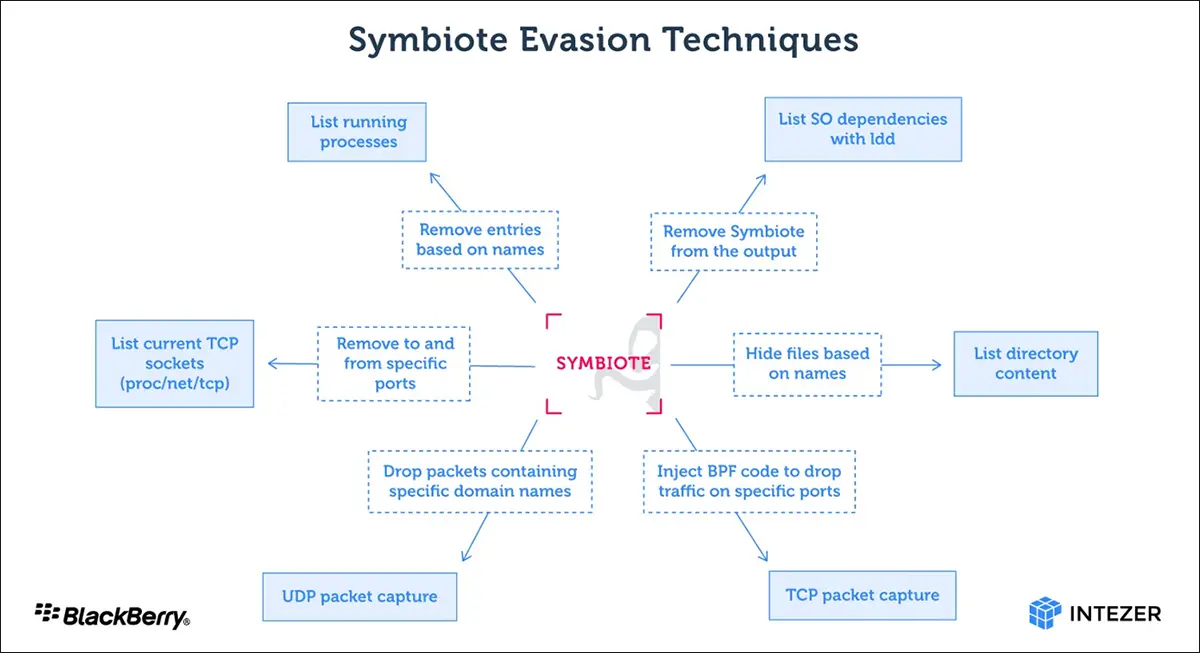
The difference between symbiote and other Linux malware we usually encounter is that it needs to infect other running processes to cause damage to the infected machine. It is not a stand-alone executable that runs to infect the machine, but a shared object (so) library that uses LD_ Preload (t1574.006) is loaded into all running processes and parasitically infects the machine. Once it infects all running processes, it will provide the threat participants with rootkit function, the ability to obtain credentials and remote access.
Security experts continue to explain why symbiote malware is difficult to detect:
Once the malware infects a machine, it will hide itself and any other malware used by the threat participants, making the infection difficult to detect. Because malware hides all files, processes, and network artifacts, performing real-time forensics on an infected machine may not find any problems.
In addition to the rootkit function, the malware also provides a backdoor for attackers to log in as any user on the machine with a hard coded password and execute commands with the highest privileges.
Because it is very cryptic, symbiotic infections are likely to "execute under scanning". In our research, we have not found enough evidence to determine whether symbiote is used for highly targeted or widespread attacks.
When the administrator starts any packet capture tool on the infected machine, BPF bytecode is injected into the kernel to define which packets should be captured. During this process, symbiote first adds its bytecode so that it can filter out the network traffic that it does not want the packet capture software to see.
Symbiote can also use a variety of technologies to hide its network activities. This is the perfect cover to allow malware to obtain credentials and provide remote access to threat participants.